top of page

Enhancing Cybersecurity Through Collaborative Threat Intelligence Sharing
Rapid Threat Detection and Response, Risk Management and Prioritization, Incident Response and Cybersecurity Strategies, Vulnerability Manag
Jan 8, 2024


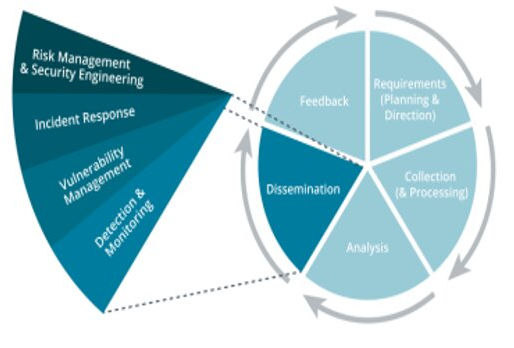
The Comprehensive Cycle of Threat Intelligence: Understanding and Mitigating Cyber Threats
Threat Intelligence is the process of gathering, analyzing, and applying information about potential or current cybersecurity threats.
Jan 7, 2024


Understanding the Threat of Process Masquerading in Cybersecurity
Process masquerading in cybersecurity stands as a critical tactic employed by threat actors to elude detection and execute malicious activit
Jan 7, 2024


Significance of Unusual Parent-Child Process Relationships in Detecting Malicious Activities
Parent-child process associations are pivotal in detecting potential threats within system operations. A child process, typically executed b
Jan 7, 2024


Proxy Logs Anomaly Hunting - CSOC Analyst
Proxy Log Examination for Data Breach Detection. Local to Remote Traffic Analysis and Threat Detection Strategies on Proxy Logs. Surveillan
Jan 5, 2024


DNS Logs Anomaly Hunting: Strengthening Cybersecurity with Insightful Analysis
Analyzing DNS logs aids cybersecurity experts in detecting unusual activities within a network, preventing threats, and bolstering defenses
Jan 5, 2024


Anomalies in Local to Local Connections - Firewall Logs
Enhanced Cybersecurity: Detecting Anomalies in Network Activities on Firewall Logs. Local to local anomalies detection
Jan 5, 2024


Anomalies in Remote to Local Connections - Firewall Logs
anomaly hunting within firewall logs, this article serves as a guide for cybersecurity experts, particularly in detecting remote to local at
Jan 5, 2024

Anomalies in Local to Remote Connections - Firewall Logs
Cyber Security Operation Centers (CSOCs) serve as critical defenders against modern cyber threats, particularly by scrutinizing and interpre
Jan 5, 2024


Common Linux Command Line Errors and How to Resolve Them
Errors encountered on the Linux command line often stem from mistyped commands, incomplete parameters, or system-related issues. These error
Jan 5, 2024


Steps to Build a Career in CSOC - Cyber Security Operations Center Analyst
Building a successful career in Cyber Security Operations Center (CSOC) demands not only technical prowess but also a continuous thirst for
Jan 5, 2024


C2 Server Detection from Operations Center Perspective via APT - CSOC APT Detection
For example, APT39 is a threat group known for conducting cyber espionage supported by the Iranian Ministry of Intelligence and Security und
Jan 4, 2024

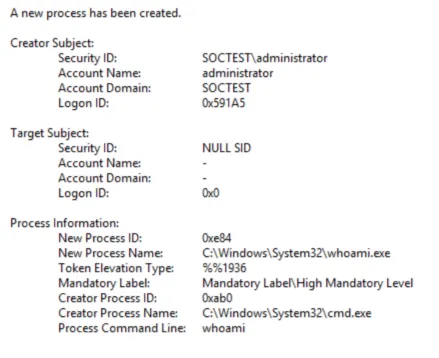
Malicious Process Detection 1 — Log Analysis — Security | Sysmon | T1055
With the malicious process detection blog post, I will explain what we should pay attention to when analyzing the event through the existing
Jan 4, 2024


My CSOC Journey - Cybersecurity as an Associate Degree Graduate
Inception to Finding a Job in the Field of Cybersecurity as an Associate Degree Graduate
Jan 4, 2024
bottom of page
